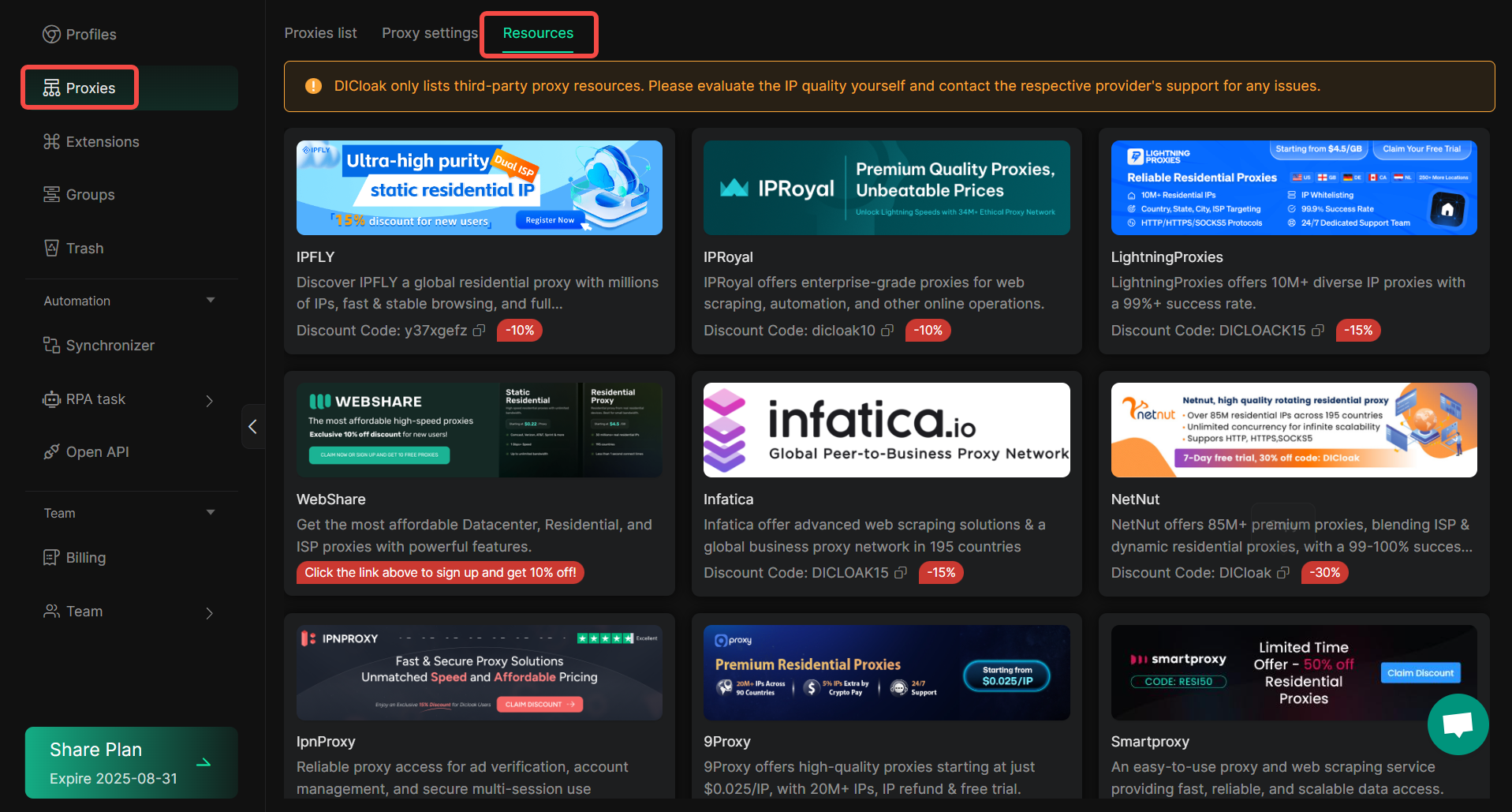
1. Optimization of the Proxies Resources Page
In [Proxies], DICloak has newly launched [Resources], and you can select the required proxies service according to your needs.
However, we need to remind you that DICloak only displays third-party proxy resources. You need to judge the quality of the IPs yourself, and if there are any issues, you need to contact the customer service of the corresponding proxy service provider.
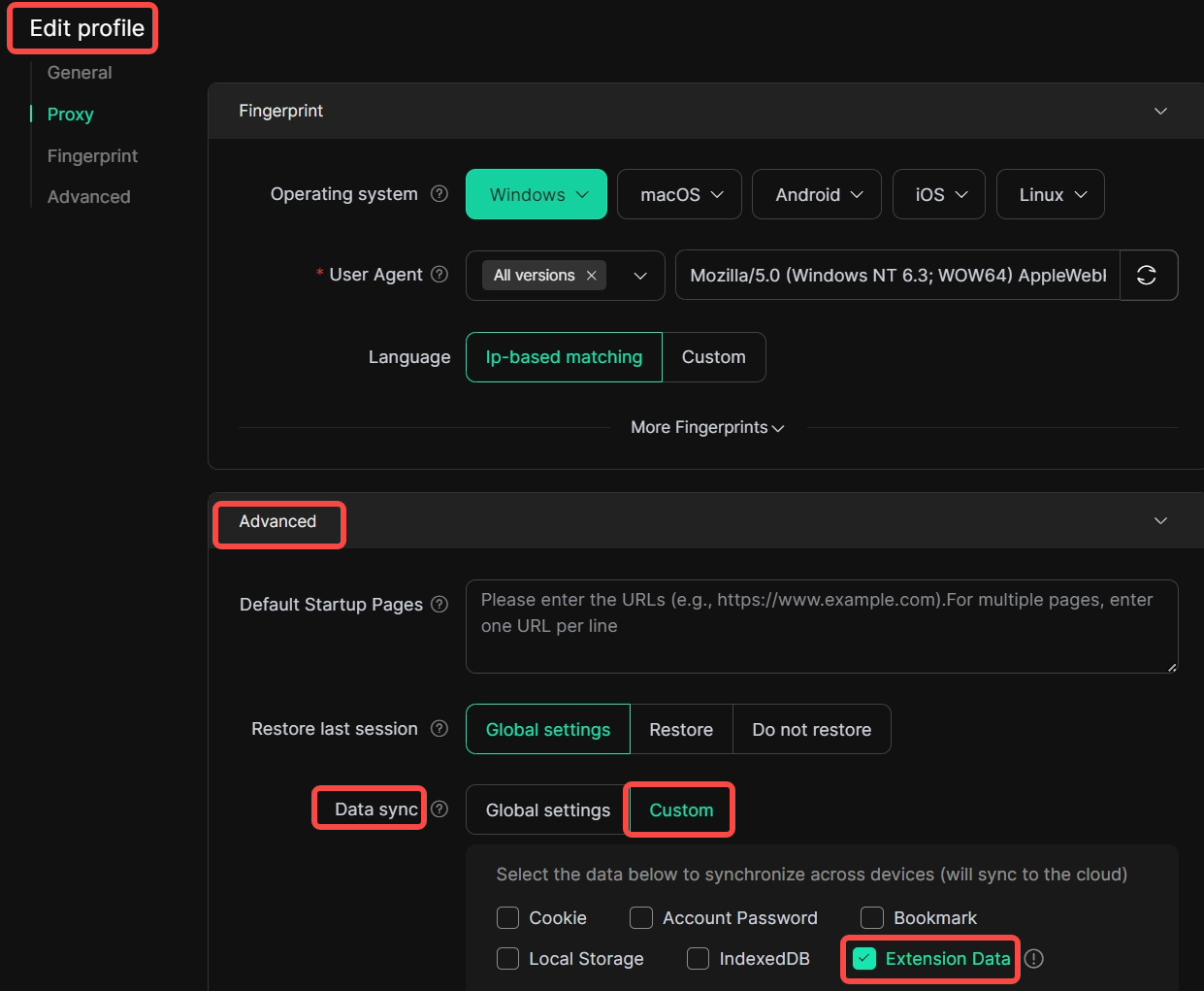
2. Extension Data Synchronization
For the profiles you have created, enter the [Edit profile] interface, go to [Data sync] under [Advanced], select [Custom], check [Extension Data], and you can synchronize the extension data to the cloud.
Usage Scenario: If you need to open this profiles across devices and use extensions, you can choose to sync extension data to the cloud (note that if you use a cryptocurrency wallet extension, it is not recommended to enable sync). When you or your team members open these profiles across devices, the extension data will be synced from the cloud to the new device, thereby enabling multi-person cross-device collaboration.
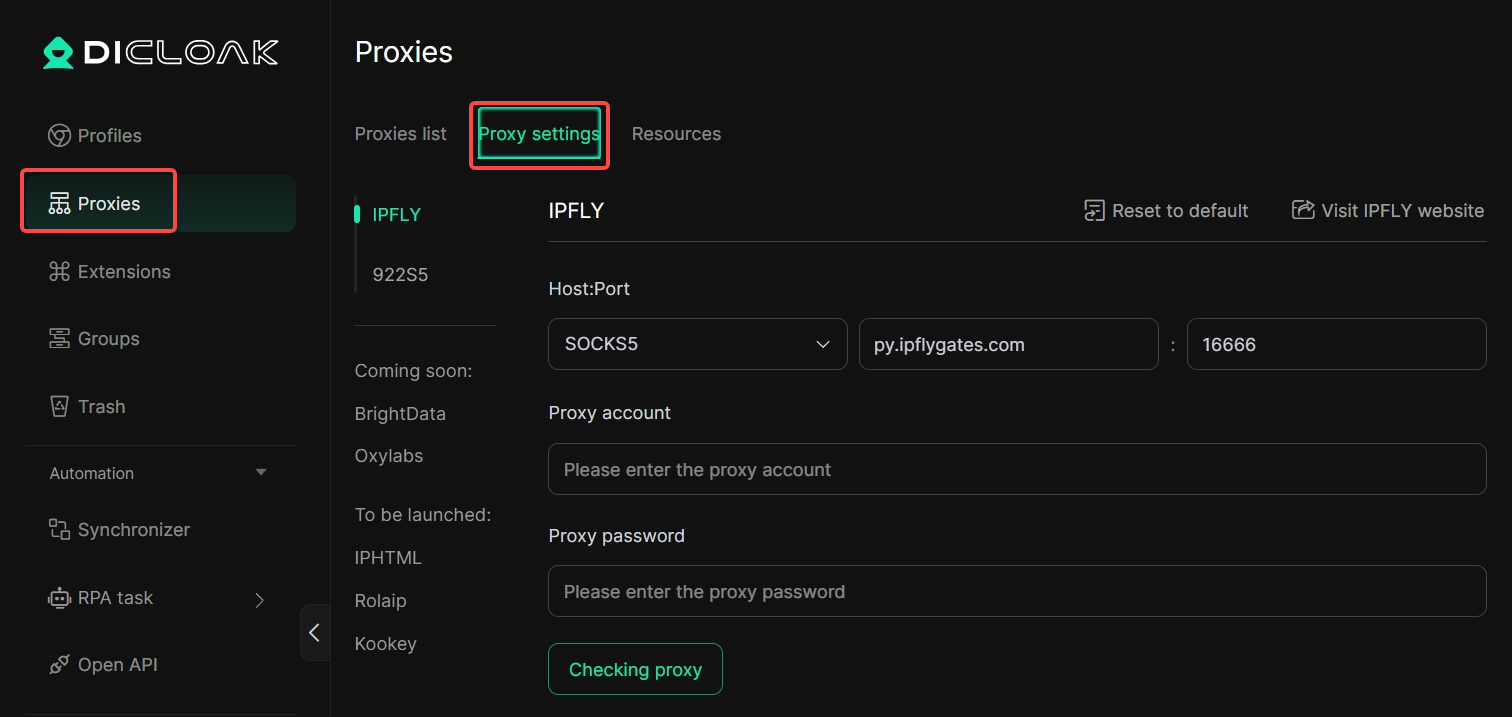
3. Proxies Supports Dynamic Proxies Setting
In [Proxies], DICloak supports you in performing [Proxy Settings].
Usage Scenarios: You can set up a dynamic proxy to implement IP address rotation, effectively bypassing the anti-crawling mechanism of the target website and avoiding being blocked due to a large number of requests from a single IP. In large-scale web crawling and data acquisition, a dynamic proxy allows each request to use a different egress IP, significantly improving the success rate and stability of data collection.
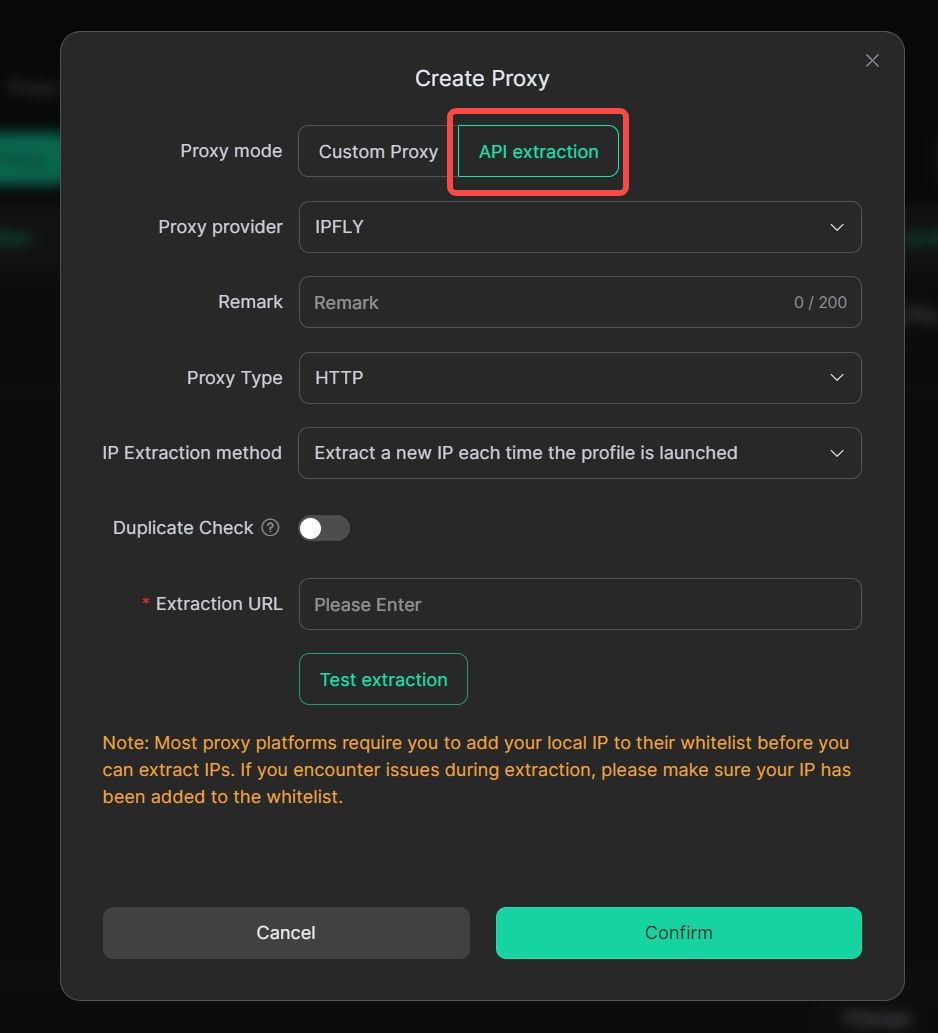
4. Proxies Supports API Extraction
In [Proxies]>[Create Proxy], you can select the Proxy method of [API extraction].
Usage Scenario: When configuring a proxy, you can choose the [API extraction] method, selecting to extract a new IP each time the profiles is opened or when the IP becomes invalid according to your needs, eliminating the need for cumbersome manual operations.
5. UI Interface Optimization
In this UI upgrade, optimizing the menu bar structure and the layout of the profiles list interface was higher on the priority list of optimization, bringing you a more concise and clear experience.
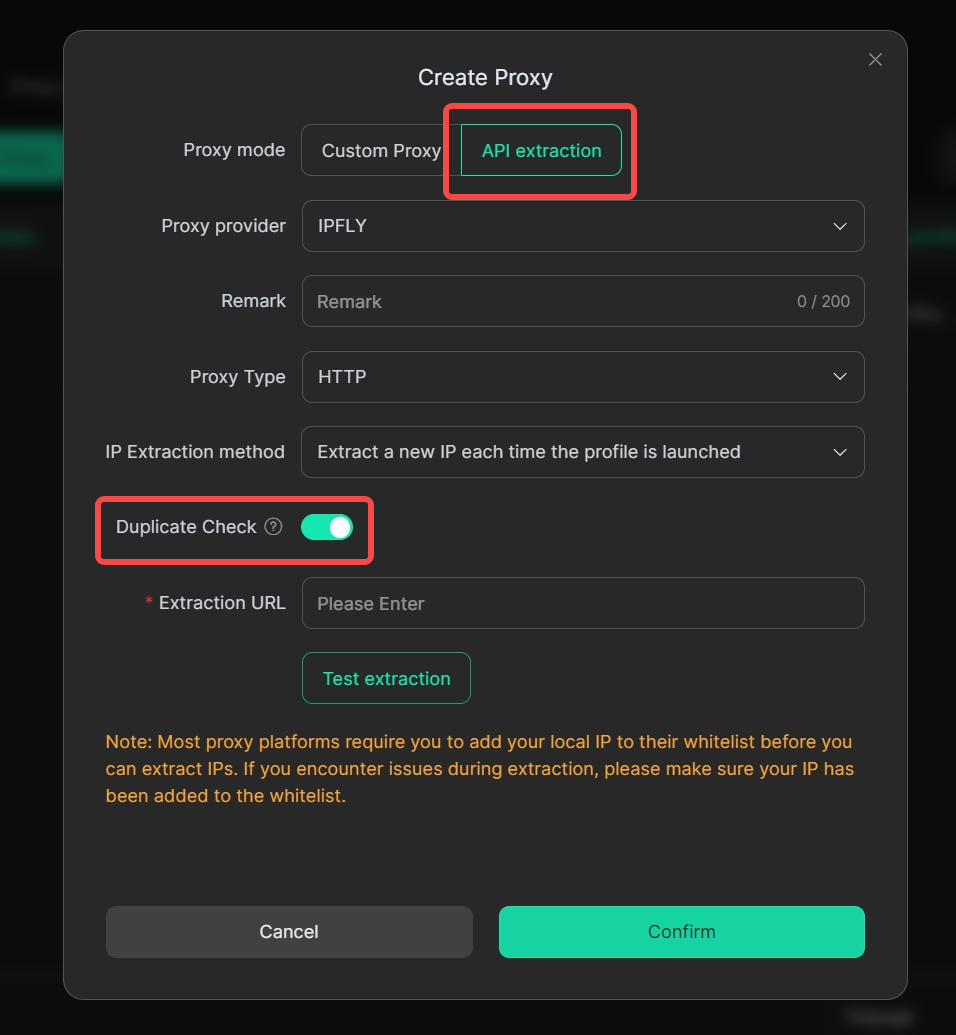
6. API Extraction Supports Duplicate Verification
In [Create Proxy], select [API extraction] as the proxy method, and you can enable [Duplicate Check] to help you filter out already extracted proxy addresses during the proxy extraction process.
Usage Scenario: If you choose to configure a proxy via API, you can enable [Duplicate Check] to help you avoid using the same IP repeatedly across multiple profiles, which could lead to account association, being identified by the platform, and ultimately being banned.
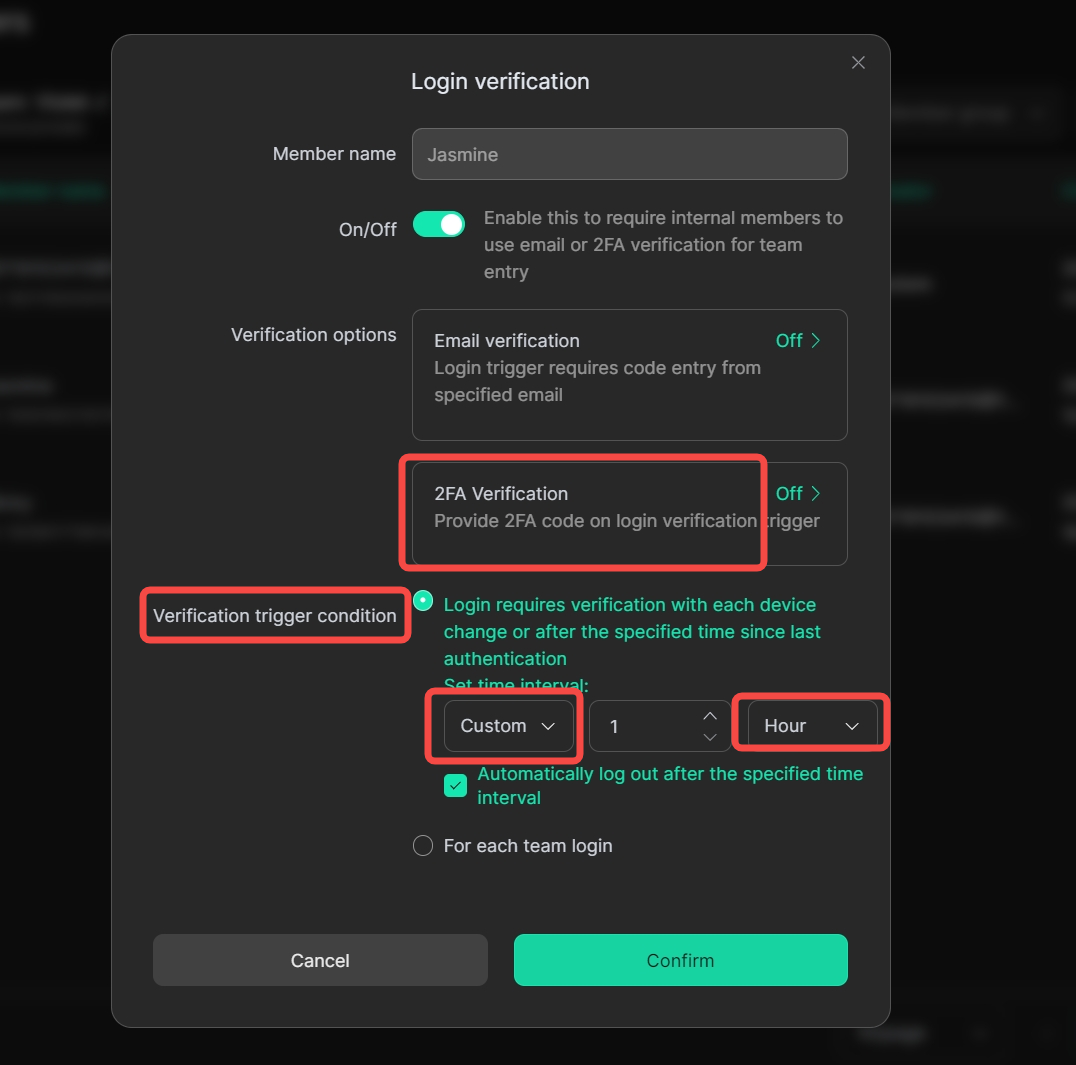
7. Login Verification Adds Hourly Dimension Condition
In the [Login verification] settings for internal members within [Members], you can enable verification permissions, requiring internal members to undergo email verification or 2FA verification when accessing the current team. Among them, in [Verification trigger conditions], you can select [Custom] and set the time interval to [Hour].
Usage Scenario: For shared account scenarios, we can provide your customers with a 1-hour account trial experience, thereby increasing paid conversions.
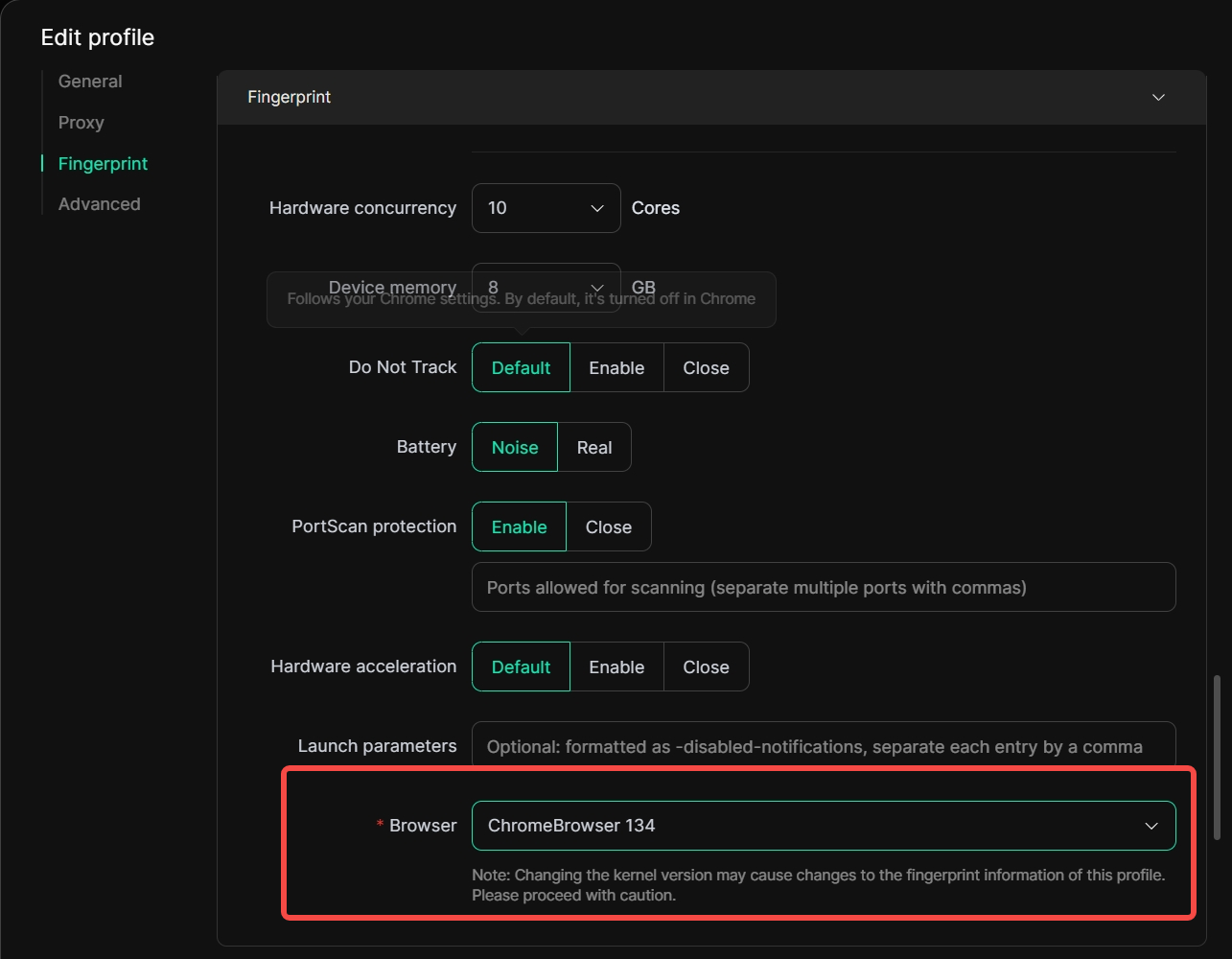
8. Browser kernel upgrade (version 134)
[Profiles]>[Edit profile], in [Fingerprint], scroll the page to the bottom, and you can update the kernel to version 134 at [Browser] to obtain a better browsing experience.
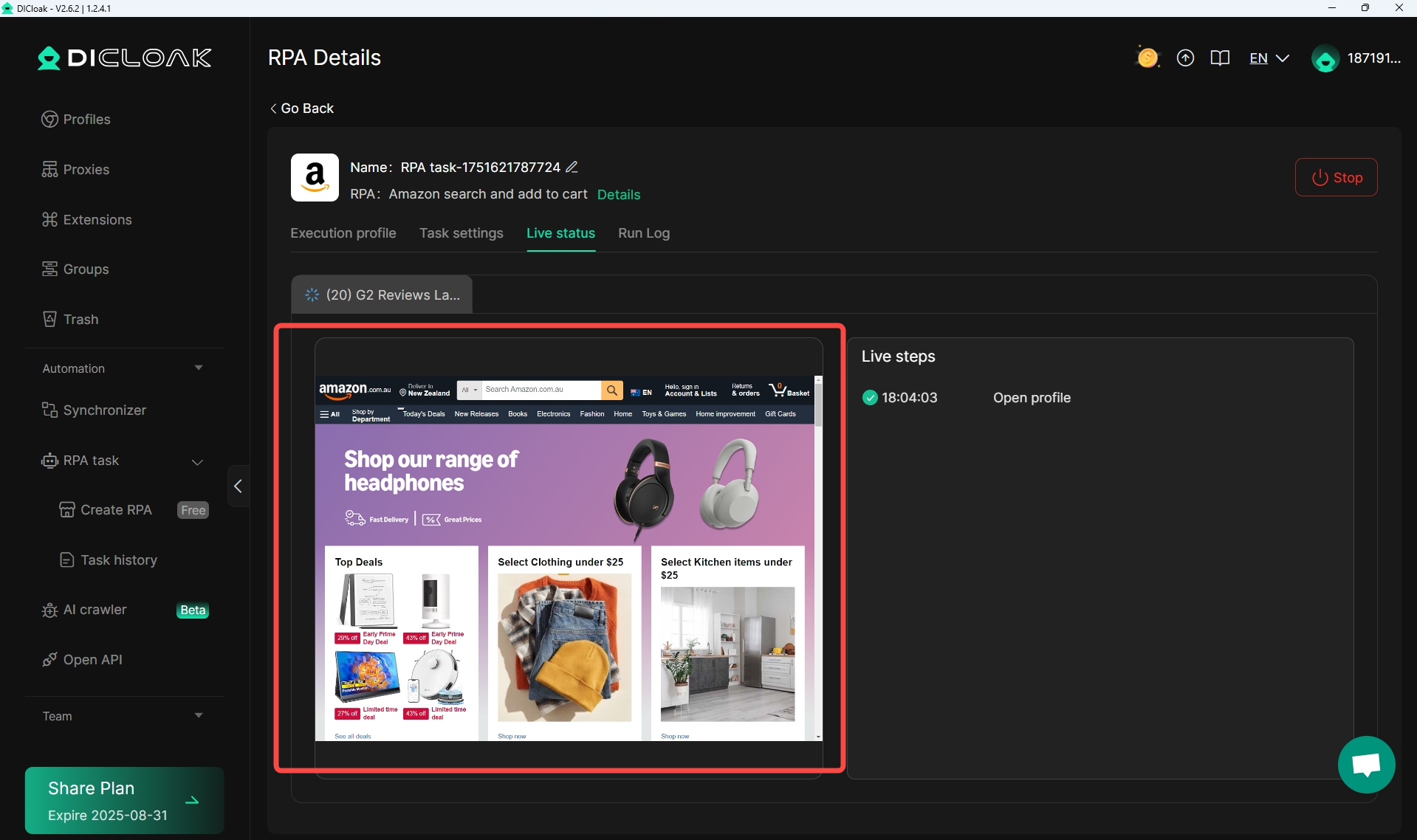
9. RPA Function Upgrade
In [Automation]> [Create RPA], DICloak has upgraded the RPA functionality. 1) Added multiple profiless to run the same RPA tool; 2) Allows for independent configuration of various parameters; 3) New [Live status] added, enabling you to observe task operation in real time; 4) New [Run Log] added, allowing you to view operation history. Additionally, if the existing RPA tools fail to meet your requirements, you can contact DICloak’s customer service team to customize a dedicated RPA tool.
Usage Scenario: When running an RPA tool in DICloak, you can monitor the task execution in real-time, ensuring that tasks are carried out according to the pre-determined plan, improving work efficiency, and reducing errors. Meanwhile, you can click on [Run Log] to view the running history of the RPA tool at any time.
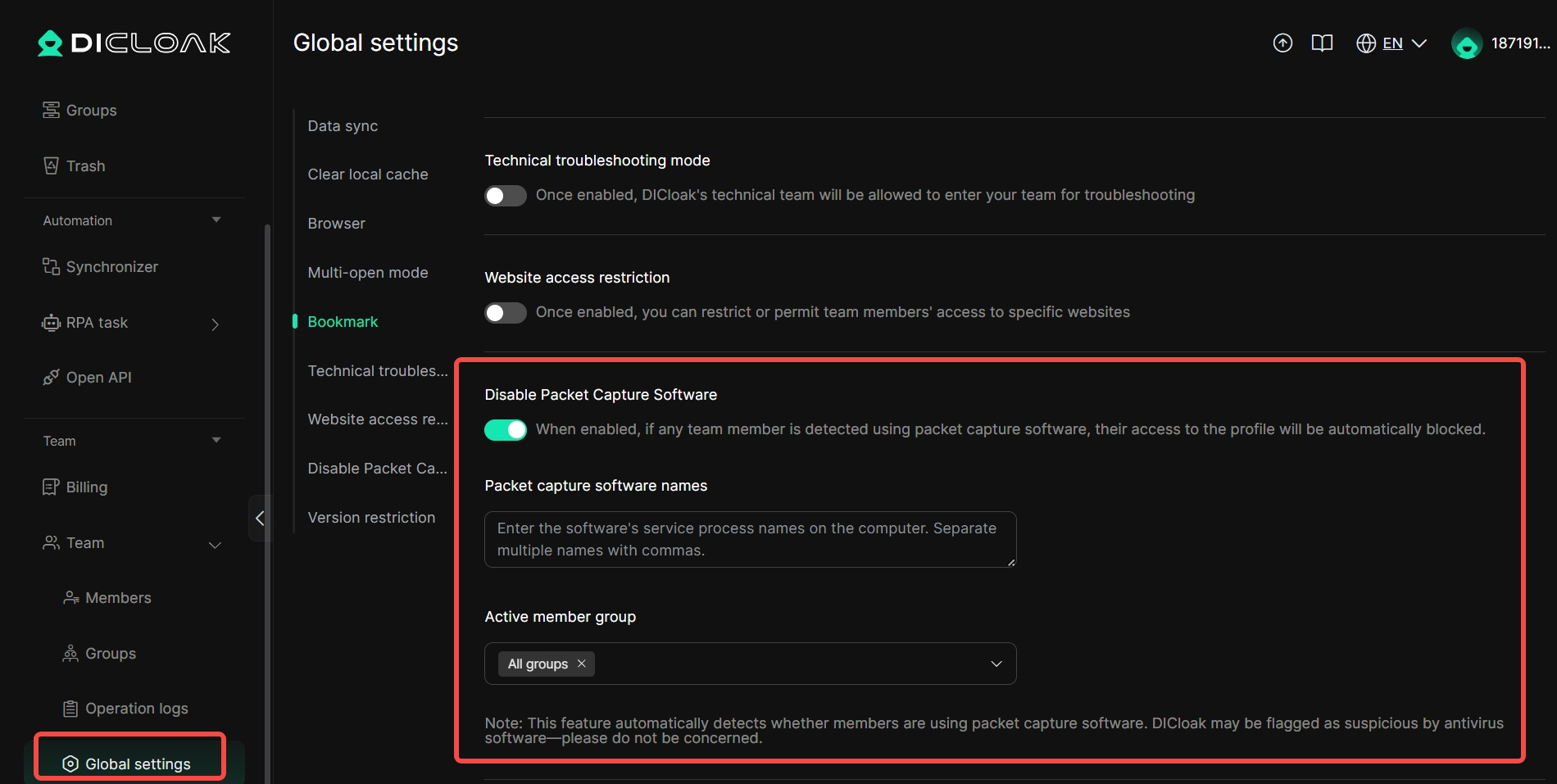
10. Prohibit packet capture tools
In [Team]> [Global settings], you can enable [Disable Packet Capture Software]. After enabling, if it is detected that a current team member is using packet capture software, they will be automatically prohibited from accessing the profiles.
Usage Scenario: When you conduct account sharing services, you can enable [Disable Packet Capture Software] to prevent internal members from using packet capture tools to obtain proxy information, account passwords, etc., thereby protecting your information security.